Windows NT 4.0:4.0.1381.7097
跳转到导航
跳转到搜索
 |
|
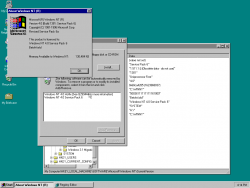
| Windows NT 4.0 4.0.1381.7097 | |
| 内核版本 | 4.0 |
|---|---|
| 架构 | Alpha, x86 |
| 版本 | Update Package |
| 编译日期 | 2001/7/16 |
| 版本字串 | 4.0.1381.7097 |
2001年7月26日发布。
Windows NT 4.0 Service Pack 6a后安全更新的最终版本[1]。
修复内容列表
- 241041 Enabling NetBT to open IP ports exclusively
- 243649 MS99-047: Unchecked print spooler buffer may expose system vulnerability
- 243835 MS99-046: How to prevent predictable TCP/IP initial sequence numbers
- 244599 Fixes required in TCSEC C2 security evaluation configuration for Windows NT 4.0 Service Pack 6a
- 246045 MS99-055: Malformed resource enumeration arguments may cause named pipes and other system services to fail
- 247869 MS00-003: Local procedure call may permit unauthorized account usage
- 248183 Syskey tool reuses keystream
- 248185 Security Identifier enumeration function in LSA may not handle argument properly
- 248399 MS00-007: Shared workstation setup may permit access to Recycle Bin files
- 249108 Registry data is viewable by all users during Rdisk repair update
- 249197 Internet Explorer does not allow use of single SGC certificate with 128-Bit encryption for virtual sites
- 249863 SGC connections may fail from domestic clients
- 249973 MS00-005: Default RTF file viewer interrupts normal program processing
- 250625 MS00-024: Default registry key permissions may allow privilege elevation
- 252463 MS00-006: Index server error message reveals physical location of Web folders
- 257870 Malformed print request may stop Windows 2000 TCP/IP Printing service
- 259042 Handle Leak in WinLogon after applying Windows NT 4.0 Service Pack 6
- 259496 MS00-008: Incorrect registry setting may allow cryptography key compromise
- 259622 MS00-0*27: Command processor may not parse excessive arguments properly
- 259728 MS00-0*29: Windows hangs with fragmented IP datagrams
- 259773 MS00-003: Incorrect response to local procedure call causes "Stop" error message
- 262388 Denial-of-service attack possible from Linux RPC client
- 262694 MS00-036: Malicious user can shut down computer browser service
- 264684 MS00-040: Patch for "Remote Registry Access Authentication" vulnerability
- 265714 MS00-095: Windows NT 4.0 SNMP registry entries are readable
- 266433 MS00-070: Patch for numerous vulnerabilities in the LPC port system calls
- 267858 "Memory could not be read" error message while doing file operation
- 267861 MS00-095: RAS registry modification allowed without administrative rights
- 267864 MS00-095: MTS Package Administration Key includes information about users
- 268082 DNS SOA record may reveal Administrator account name
- 269049 MS00-052: Registry-invoked programs use standard search path
- 269239 MS00-047: NetBIOS vulnerability may cause duplicate name on the network conflicts
- 271216 Fix for e-mail issues between 128-bit and 56-bit encryption using French regional settings
- 274835 MS00-083: Buffer overflow in Network Monitor may cause vulnerability
- 275567 MS00-091: Multiple NetBT sessions may hang local host
- 276575 MS00-094: Patch available for "Phone Book service buffer overflow" vulnerability
- 279336 MS01-003: Patch available for Winsock mutex vulnerability
- 279843 Some system named pipes are not created with appropriate permissions
- 280119 MS01-008: A patch is available for the NTLMSSP privilege elevation vulnerability
- 283001 MS01-009: Patch available for malformed PPTP packet stream vulnerability
- 293818 MS01-017: Erroneous VeriSign-issued digital certificates pose spoofing hazard
- 294472 MS99-057: Index Server search function contains unchecked buffer
- 296185 MS01-025: Patch available for new variant of the "Malformed Hit-Highlighting" vulnerability
- 298012 MS01-041: Malformed RPC request can cause service problems
- 300972 MS01-033: Unchecked buffer in Index Server ISAPI extension can enable Web server compromise
- 303628 Relative path issue can allow program to be run under the System context
后安全更新中的IIS修复补丁
- 252693 Chunked encoding request with no data causes IIS memory leak
- 254142 MS00-023: 100% CPU usage occurs when you send a large escape sequence
- 260205 MS00-030: HTTP request with a large number of dots or dot-slashes causes high CPU utilization
- 260838 MS00-031: IIS stops servicing HTR requests
- 267559 MS00-044: GET on HTR file cancCause a "Denial of Service" or enable directory browsing
- 269862 MS00-057: Patch released for canonicalization error issue
- 271652 MS00-063: Patch released for malformed URL vulnerability that disables Web server response
- 274149 Cookies are not marked as SSL-secured in IIS
- 277873 MS00-086: Patch Available for "Web Server File Request Parsing" vulnerability
- 285985 MS01-004: Patch available for new variant of File Fragment Reading via .HTR vulnerability
- 295534 Superfluous decoding operation can allow command execution through IIS
在 2001年5月14日的微软知识库文档中列出的亦包含在后安全更新的补丁
- 297860 MS01-044: IIS 5.0 Security and post-Windows NT 4.0 SP5 IIS 4.0 patch rollup
后安全更新引入的问题及其修复补注
对于Compaq阵列控制器用户
如果您已经从Compaq网站,Compaq FTP站点或Compaq SmartStart安装了Compaq阵列控制器驱动程序(Cpqarray.sys),请参阅微软知识库中有关Compaq阵列控制器和Windows NT 4.0 SRP的以下文章:
305228 应用Windows NT 4.0安全汇总包后出现“ STOP 0xA”
数字签名问题
如果您运行的是Internet Explorer 5.5 Service Pack 2(SP2)或Internet Explorer 5.01 Service Pack 2(SP2),并且您访问使用安全套接字层(SSL)的任何安全网站(https://),请参阅微软知识库:
305929 安装Windows NT 4.0安全汇总包后,出现“此证书具有无效的数字签名”的错误消息
Microsoft IntelliPoint用户
如果使用2.2之前的Microsoft IntelliPoint版本,则在安装SRP之前,请参阅微软知识库中的以下文章:
305462 在安装Windows NT 4.0安全汇总套件后,滑鼠和键盘停止运作
HP NTLock用户
如果使用HP NTLock,请参阅微软知识库中的以下文章:
311860 安装Windows NT 4.0安全汇总包后,Hewlett-Packard NTLock服务无法启动
其他未明确在支持文档中标注已修复的补丁
299273 从MS01-026安全公告应用修复后,UPN登录选项不起作用
269430 双击SSL安全连接中的锁定图标后不正确的错误消息